Volume Lock 2 2 Crack 3
 Crazy Penguin Catapult, Launch a high-flying, penguin-rescue mission. Crazy Penguins Wars. You are in:Penguin Games. Crazy Wars are going on between penguins from all over the world. After you pass the basic course of how to walk.
Crazy Penguin Catapult, Launch a high-flying, penguin-rescue mission. Crazy Penguins Wars. You are in:Penguin Games. Crazy Wars are going on between penguins from all over the world. After you pass the basic course of how to walk.
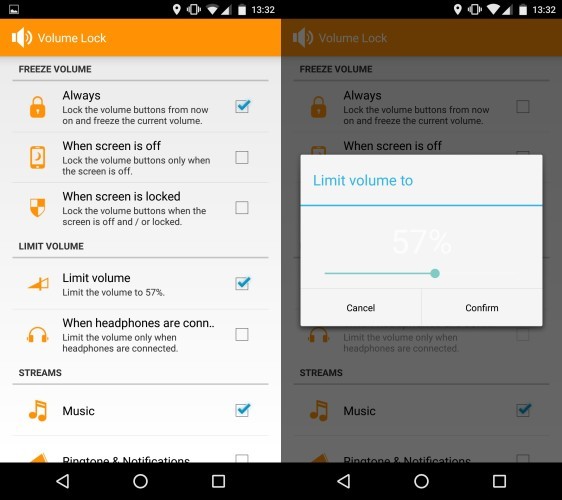
Control the volume level of your PC and prevent other applications from changing the volume. (Link) VolumeLock volume lock volumelock crack volume lock 1.8 volumelock 2.3 volumelock 1.7 volumelock 1.7 crack volumelock 2.2 serial volumelock serial volumelock 2.2 volumelock 2.3 crack Download VolumeLock v2. -- theres no risk to try.
Not a whole lot you can do about this. There is no other way and you will have to do a hard reset This setting erases all data from your device, including your Google or other email account settings, system and application data and settings, and downloaded applications.
After a reset, you’ll be prompted to set up your device the next time you turn it on. With the device off, press and hold Volume Down and Power. Release the Power button when you see the Samsung logo, but continue to hold Volume Up until the recovery screen appears. Use the Volume buttons to navigate the menu and select wipe data / factory reset. Press Home to choose the selection. Press Volume Up continue. Sage 50 accounting 2014 keygen crack.
This answer might or might not help. Unfortunately I will refer to a document I read online recently but failed to bookmark, so consider this is more of an introduction to a unicorn than an answer. Facing a similar problem with forgotten pattern and no clue which of many gmail accounts the phone was associated with, I tried every gmail account I could think of and admitted defeat.
I halfway think there was a bug in my old Motorola's software that meant I couldn't have recovered access even if I did know the gmail address, but that's neither here nor there. Defeated, yes, but still breathing. I hate nothing quite as much as destroying data, so I did not want to do a hard reset. I decided to find out if smudges or fingerprints on the phone's screen might somehow carry a memory of the pattern I routinely used to log in to the phone in the past. I entered various search terms into Google and eventually found that some security researchers, possibly in Israel, had published a white paper on the topic. I was overjoyed, but didn't have time to read the whole thing.
I didn't try it and still don't know if it will work for me. (In my case the phone has been handled so much since the last time I logged in that it's unlikely.) I remember that they figured out how to shine light on the phone from a particular angle, but not the angle or anything about the light itself. So, a lame 'hope that helps' to close with, and a promise to look for the paper again if I have some time later on this afternoon. Maybe you can find it using Google. I should have asked you if you have tried to recover your gmail password on an internet-connected computer, phone, or tablet. If you can't use someone else's device, an Internet cafe of a FedEx store will rent you time online.Typing mail.google.com into a web browser will either bring up the gmail account of someone who is still logged in (in which case, the simplest thing is to log them out in order to reach the gmail login page) or offer the gmail login screen.
Look for the 'forgot password' link and do what's required to recover your password. Then log out. All of that assumes that restoring access to your Gmail account will get you back into your phone. I finally return, but with a different article of interest first. This is a bogus click bait article of which Slashdot should be ashamed. The headline says you can crack an Android login pattern in five tries.
The article adds that you must first observe the user as she unlocks the device herself! This here is the one I was looking for. It's actually from UPenn, with a first author whose last name is Aviv, which is why I associated it with Israel. Link: Title: Smudge Attacks on Smartphone Touch Screens Adam J.
Aviv, Katherine Gibson, Evan Mossop, Matt Blaze, and Jonathan M. Smith Department of Computer and Information Science – University of Pennsylvania They cover: - conditions under which smudges are easily extracted (most are extractable) -usage situations that interefere with pattern ID (pattern smudges continue to be recognizable) -using what they learned to guess an Android password pattern.